As society relies more heavily on technology for everyday tasks, the need for professionals who understand how to build, secure, and assess information systems has become crucial.
This post is for the person that is willing to put in the work required to become a world class information security professional. It assumes that you possess a degree of technical knowledge and have a desire to improve the state of an evolving art. Most importantly, it assumes you are willing to commit to a journey of constant learning. The information is relevant for both college graduates entering the market and seasoned professionals. It’s for anyone wishing to take their career in a new direction.
My goal is to provide a no-fluff guide towards becoming a highly sought-after information security professional. I dislike books that take an encyclopedic approach to what can be conveyed in a paragraph. To paraphrase the maxim often attributed to Einstein: “Everything should made (or explained) as simply as possible, but not simpler.”
Let’s get started.

Are you an Architect or an Engineer?
I consider there to be two major paths within Information Security: the Engineer and the Architect.
While still highly technical, the Architect takes a big picture approach when assessing the security of an information system. They are the types who first understand the threats specific to the business vertical. They realize the importance of balancing costs with effective security. Architects have the challenging job of conveying information security concerns in a way that allows senior management to make informed business decisions around risk. A good Architect is effective at explaining complicated issues in a manner that is useful to leadership. At a minimum, they have knowledge that is “an inch deep and a mile wide.”
Conversely, the Engineer takes an “inch wide and mile deep” approach to a given discipline. This is the domain where exploit writers, penetration testers, and incident response professionals live. It consists of highly focused skill sets that are ever-changing. These are the types of people that present or teaching at security conferences like Black Hat and Defcon.
Builder or Breaker?
For those taking the Engineer route, determine whether your bent is towards being a “builder” or a “breaker.” People with the “builder” mindset are far more prevalent, and they tend to focus on network and system defense. Builders tend to perform tasks such as firewall and intrusion detection/prevention system management, security patching, and security event monitoring. Those with the “breaker” mindset tend to gravitate towards work that involves reverse engineering, penetration testing, and exploit development. They are the ones that disassembled their toys as children in the interests of understanding what made them tick.
Along military lines, if the Architect is a commanding officer of an information security program, the Engineer is the Navy SEAL. The Engineer possesses the skill set required to successfully execute very specific tasks. Architects are better compensated than Engineers. That said, an experienced and highly technical Engineer can earn anywhere from $150k – $250k USD per year. Certainly nothing to sneeze at.
Core Skills: The Information Security Lattice
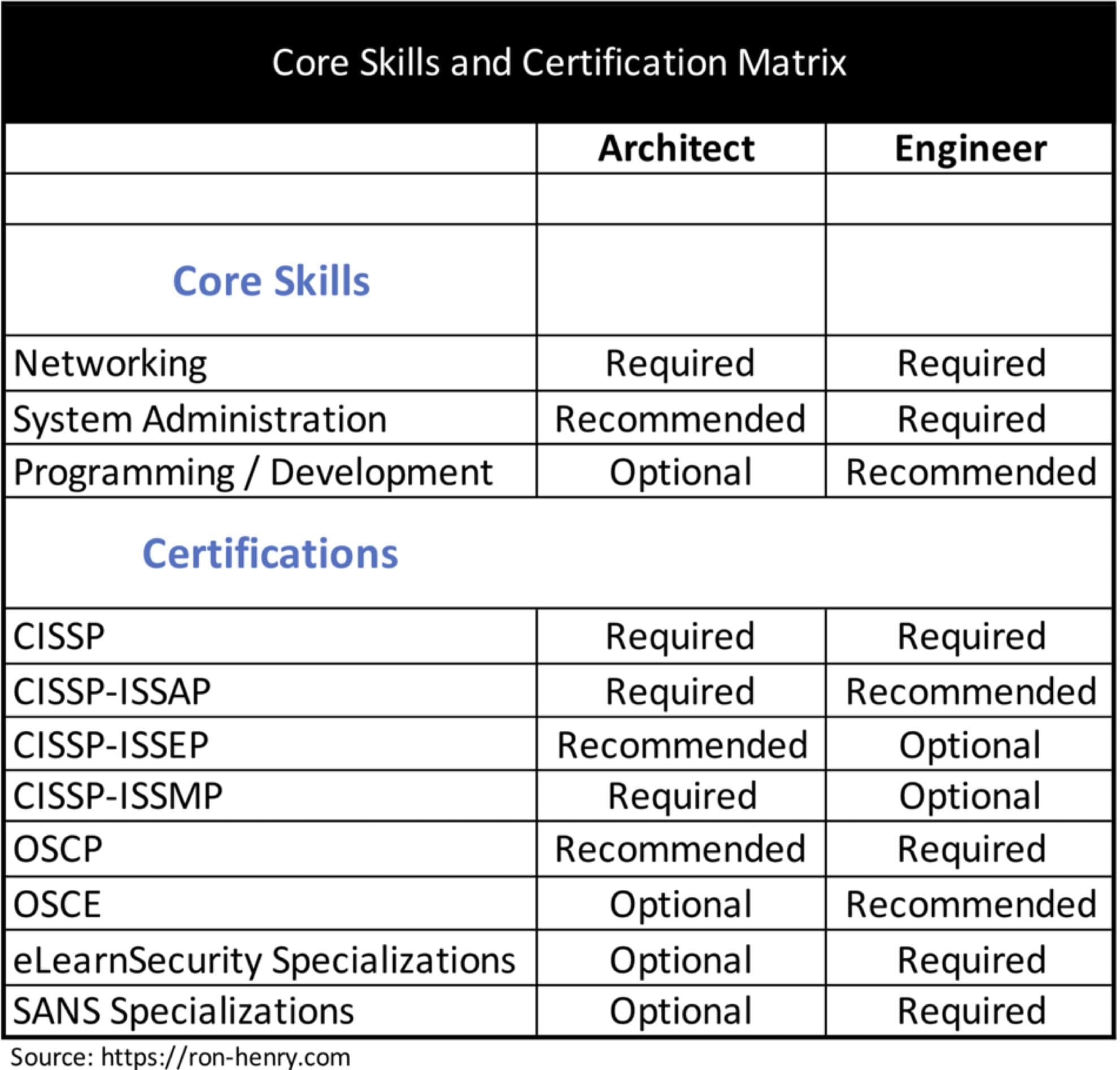
The best information security professionals possess knowledge in three major areas that I like to call The Information Security Lattice. The components of the lattice are Networking, System Administration, and Programming/Application Development. These core areas are present in every information system and deep knowledge of at least one of them is crucial towards being effective as an InfoSec professional. As I think back over my years in this field, every great security professional I’ve worked with was a Jedi in at least one of these three areas.
Let’s dig a bit deeper into each of them.
Networking
Networking is the underappreciated glue stitching the systems of the Internet together. At more than a basic level, one needs an understanding of how computers communicate and the underlying protocols that make network communications possible.
Acronyms such as TCP/IP, DNS, ARP, TCP, UDP, TLS, ICMP, MAC, WPA, etc. shouldn’t cause your eyes to glaze over. If they do, go buy yourself a good book (or five) and start reading. Networking equipment has become so inexpensive in recent times that it would also be good to build a small network at home. A home lab will give you a safe place to experiment with different configurations. Because networking is such a core aspect of information security, all effort spent improving your knowledge in this space will pay dividends over time.
So you understand how computers communicate. You understand ARP poisoning with the best of them. You also grasp the core differences and security concerns around connection and connectionless protocols. Awesome. Now it’s time to focus on the endpoint. It is important to understand how its software is configured to process the information it receives. This is where understanding system administration comes in.
System Administration
System administration is a field within itself. That said, a good information security professional should understand the aspects that impact security. For example, do you understand the differences between how system passwords are stored on Windows and *nix systems? If you had to investigate an attack against a web server, which types of logs would you need and where would you find them? How are firewall rules added/removed and stored? These and countless other topics encompass the subfield of system administration. Knowledge in this space will allow you to ask intelligent questions of the actual system administrators. It will make you much more effective in your work.
Programming
Programming. Do “if-then-else” blocks, pointers, cache management, and the nuances of branch prediction get your juices flowing? Programming must be your thing then. Even if you never actually write software for a living, there are advantages to understanding how code written. You should know how code written in high-level languages like C, Java, or Python is translated into the bytecode executed by the system processor.
For the Engineer-type professional, time should be invested to learn at least one programming language. Python is a great starter language. It is incredibly powerful, well supported, and relatively easy to learn. Many of the tools used by exploit writers and incident responders support extending their functionality using plugins written in Python. Time invested in learning this space is well spent. Next, I recommend that you learn enough of the C programming language to where you can understand code written in it.
Most software vulnerabilities are the result of poorly written code that doesn’t properly validate user input. By having some experience around writing basic information processing routines, you will be in a much better position to catch input validation bugs. For example, you should be able to easily point out the bugs in the following poorly written program:
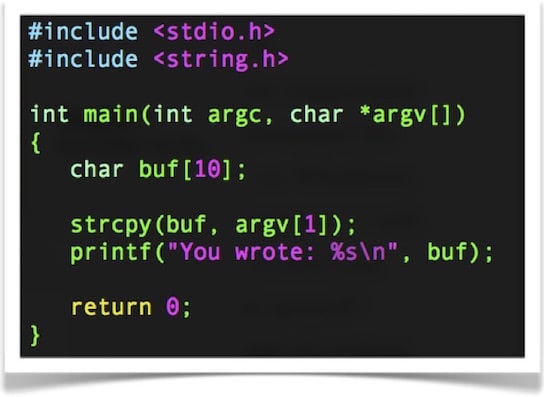
By gaining knowledge in the three primary areas of the Information Security Lattice, you will have the foundational knowledge required to recognize weaknesses in a given system. In order to identify when something is broken, you need to understand what it looks like when functioning properly. Therefore, your aim should be to regularly read books on each of these three areas in order to constantly deepen your knowledge.
Bedside Manner
While having the ability to decipher a packet capture is both fun and important, we can’t overlook the importance of being an effective communicator. The best information security professionals have the ability to explain complicated topics to those less technical. In fact, the mark of someone that truly understands a topic is being able to explain it in such a way that a layperson can grasp the concept at an elementary level.
While being an effective communicator is critical for those taking the Architect path, Engineers should also invest time improving this as well. Most good Architects were Engineers at some point. So even if security architecture isn’t your goal, time spent improving your “bedside manners” is important. Keep in mind that information security systems exist to protect business resources and intellectual property. Being able to convey concerns in a manner that shows you are not just another “techie” will allow your words to carry much more weight.
Public Speaking
A great way to become more comfortable with public speaking is by offering to give short talks on a technical subject. Most major cities have security groups that meet monthly, and this can be a great time to share what you know.
As information security professionals, we are often entrusted to identify risks to the organization. Those risks are often introduced by another group within the same company. Yikes! Being able to call someone’s baby ugly without directly saying so is just as important as being able to write an efficient Suricata/Snort signature. It’s not flashy, but developing this skill will go a long way towards senior management seeing that you are a big picture person. This is especially important for those in customer-facing roles. It applies to those performing incident response, penetration testing, and risk assessments.
Certify Your Path
Regardless of what you’ll commonly hear, certifications are important in your development as an information security professional. The right ones will open doors, as well as give potential employers confidence that the information security practitioner has real-world skills. Preparing for certification exams also often forces you to learn the nuances of a given concept that you may have overlooked in the past. While there are countless companies offering information security training, I wanted to mention the four whose courseware and certifications I have experience with.
- eLearnSecurity – https://www.elearnsecurity.com
- ISC2 – https://www.isc2.org
- Offensive Security – https://www.offensive-security.com
- SANS – https://www.sans.org
About the CISSP
Which certifications you obtain really depends on the route you plan on pursuing in your career. A core certification that all fledging information security professionals should obtain is the CISSP. The acronym stands for “Certified Information Systems Security Professional,” which is quite a mouthful. While the CISSP often gets a bad rap for not being technical enough, I feel that it’s important. The CISSP provides a wide base of knowledge that creates a solid foundation. After the CISSP, there are three concentrations that will allow you to deepen your knowledge in key areas. These are:
CISSP-ISSAP – Architecture
CISSP-ISSEP – Engineering
CISSP-ISSMP – Management
As the names imply, each concentration focuses on a single sub-domain of information security. Although the ISSAP is targeted at Architects, those taking a more technical path would still benefit from it. This is due to how deep it goes into topics like encryption, certificate management and infrastructure.
The ISSEP and ISSMP concentrations are primarily aimed at professionals in system accreditation/certification and managerial roles.
The courses offered by SANS, eLearnSecurity, and Offensive Security are all highly technical in nature. They are best-suited for those taking the Engineer route. I’m a big fan of the courses and certifications offered by eLearnSecurity and Offensive Security in particular because they require that the student actually demonstrate real-world skills in order to pass the exam. Depending on the course, the examination process entails conducting an actual penetration test, web application assessment, or reverse engineering challenge. This is a true assessment of the applicant’s ability.
If I were to break down the certifications I recommended based on path, they would be as follows:
Tying It All Together
Information security can take you in any of a number of directions. Regardless of the path you choose, realize that to become and remain among the best in the field requires a commitment to constant learning and refinement. Set the goal of reading 10–12 InfoSec-specific books per year. It will go a long way towards keeping your skills sharp.
Another great way to gain regular exposure to the current state of the art is to attend security conferences. Some of the more general conferences like Black Hat, Defcon, and ShmooCon offer talks and training on a wide range of topics. There are also more targeted conferences such as Infiltrate and ReCon that focus on system exploitation and reverse engineering. Make it your goal to attend at least one per year. In addition to being able to hear talks on a variety of subjects, these conferences are a great way to meet new people in the industry.
Realize that information security pulls a bit from many different technology areas. The major components of the Lattice (Networking, System Administration and Programming/Application Development) provide the core foundation from which to grow your skills. Understand and embrace the fact that there will always be something new to learn and that doing so will improve your ability to elegantly solve complex problems.
Although brief, I hope you found this to be useful. If you have additional questions or if I can help with anything, feel free to reach out to me.
BONUS: If you’d like a FREE PDF version of this post that is beautifully illustrated, use the form below to download a copy of it.
For a Kindle-friendly version, buy it on Amazon here. Thanks!